Ensuring Airtight HR Data Security
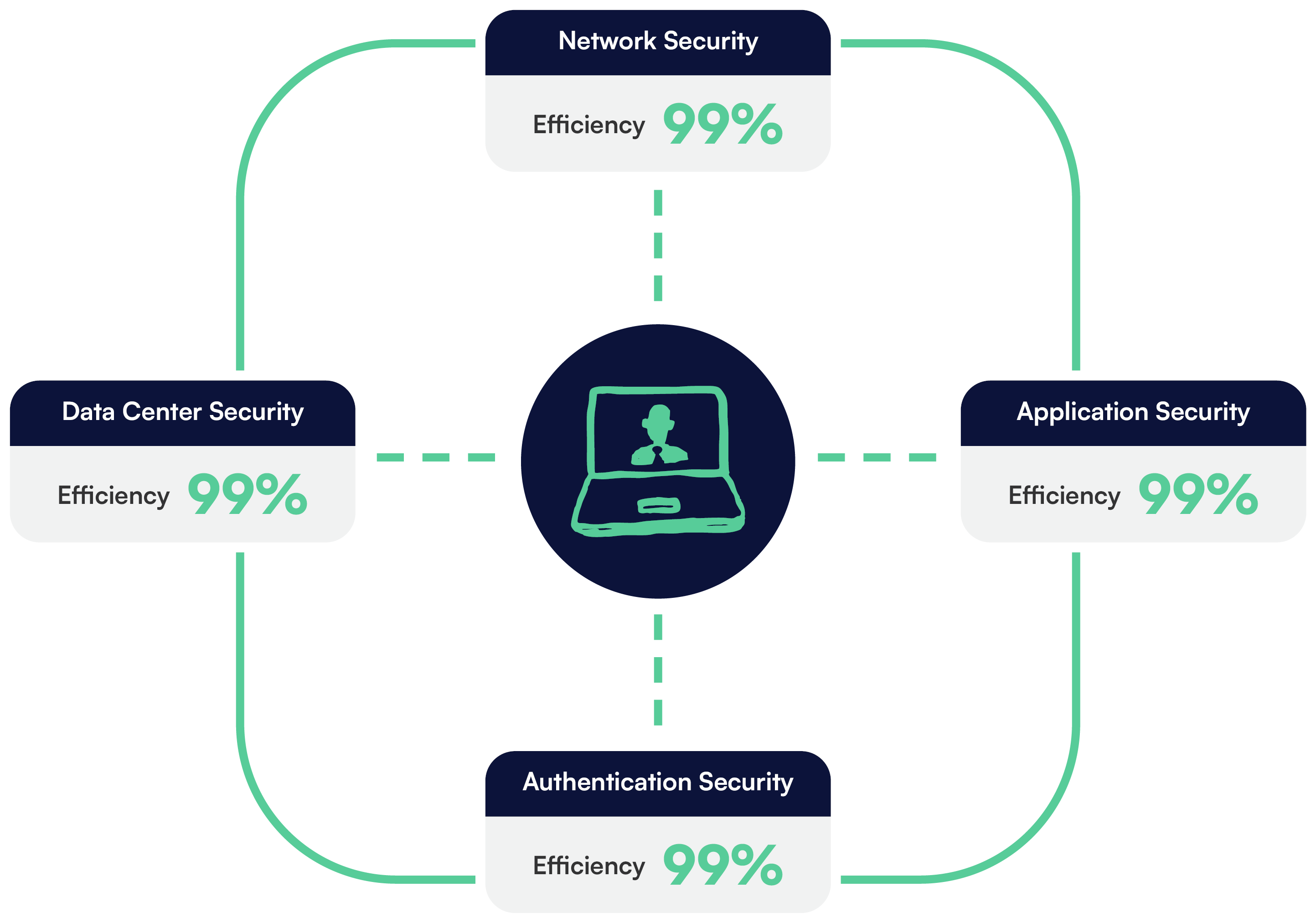
There are enough risks within employee relations. Don’t make compromising your organization’s sensitive employee data one of them. Our ironclad four-pillar approach to our platform safety is backed by security experts.
Data Security
All information and data is securely hosted within Microsoft Azure to ensure top-tier security.
Application Security
Our application undergoes rigorous development testing and processes to ensure the highest level of security.
Network Security
Our encrypted network is constantly monitored against key protection protocols and industry best practices.
Authentication Security
Our authentication options guarantee that users can securely access data meant for their eyes only, reinforcing confidentiality and data access control.
A Deep Dive Into Our Security Protocols
-
- Facilities
HR Acuity partners with Microsoft Azure to provide our data hosting infrastructure at its Tier IV SSAE-16 and ISO 27001 compliant facilities in the United States. Data center facilities are powered by redundant power, each with UPS and backup generators. - On-site Security
Microsoft data center facilities feature a secured perimeter with multilevel security zones, 24/7 manned security, video surveillance, multifactor identification with biometric access control, physical locks, and security breach alarms.
- Facilities
-
- Protection
Our network is protected by redundant firewalls, best-in-class router technology, secure HTTPS transport over public networks, regular audits, and network intrusion detection and/or prevention technologies (IDS/IPS) that monitor and/or block malicious traffic and network attacks. - Architecture
Our network security architecture consists of multiple security zones. DMZs are used between the internet, and internally between the different zones of trust. - Vulnerability and Penetration Tests
At appropriate stages in the life cycle, vulnerability scans are performed for identification of noncompliance or potential vulnerabilities. At higher-level milestones, penetration tests are performed at the application level with a qualified third-party information security expert using both automated and manual testing techniques. - Logical Access
Access to our database is restricted by an explicit need-to-know basis, utilizes the least privilege, and is regularly audited and monitored. In addition, employees with access privileges are required to use multiple factors of authentication. - Security Incident Response
Our globally distributed HR data security team is on call 24/7 to respond to alerts and emergencies. In case of a system alert, employees are trained on security response processes, including who to connect with and when to escalate. - Encryption in Transit
Communications between HR Acuity and our users are encrypted via industry best-practices HTTPS and Transport Layer Security (TLS 1.2) over public networks. - Encryption at Rest
All HR sensitive data stored with us is encrypted at rest using Transparent Data Encryption (TDE)/AD. - Redundancy
We have put network redundancies in place to eliminate single points of failure. Client data is actively replicated across primary and secondary DR systems and facilities. - Disaster Recovery
Our Disaster Recovery (DR) program ensures that our services remain available or are easily recoverable in the case of a disaster.
- Protection
-
- S-SDLC
Security and control are paramount to software development, which is why we use the HR Acuity Secure Software Development Lifecycle (S-SDLC). It’s been designed to ensure the software we produce meets compliance requirements and is free of software security glitches (to the greatest extent possible) so confidential data remains that way. - Security Training
Our system engineers regularly participate in secure code training covering OWASP Top 10 security flaws, common attack vectors and HR Acuity security controls. - QA
QA engineers review and test our code base on a regular basis. Test cases that are created to identify code vulnerabilities must pass inspection before the HR Acuity application even hits production servers. - Separate Environments
All forms of testing and user acceptance testing (UAT) environments are physically and logically separated from the production environment. We also make sure no actual client data is used in the development or test environments. - Change Management
Our S-SDLC uses an Agile/Scrum process for managing system development activity. We have also implemented change management and version control software to ensure that all system development changes are sourced from authorized requesters, validated and prioritized on business, technical and security impact. In addition, all changes deployed are scrutinized for revision control.
- S-SDLC
-
- Authentication Options
Users can sign in to our application using authenticated credentials or SSO login. User provisioning and permissioning are managed by our clients. - Single Sign-On
Single sign-on (SSO) allows us to authenticate users in HR Acuity without requiring them to enter additional login credentials. We partner with Ping One to enable SSO login for our clients via Security Assertion Markup Language (SAML). - Password Policy
We provide clients with the option to define their password change frequency as well as their repeat policy. Password length and password strength are defined based upon industry best practices. In addition, all password reset links are time-based and expire after one use or a certain length of time. We use Password Managers and Key Vaults. - Secure Credential Storage
HR Acuity user credentials are stored in the database using Bcrypt algorithms. - Access Privileges and Roles
Authorized HR Acuity Users are provided with multi-level permissions based upon user and role credentials. The flexible role-based authorization process is governed by each client to ensure data is secure and only made available to those who require access to it.
- Authentication Options
Frequently Asked Questions
-
HR Security is a function of Human Resources that not only looks at employee performance and productivity before, during and after their employment, but also ensures that confidential employee and client data remains protected.
-
Ensuring HR data security is critical because human relations professionals often deal with highly sensitive information about employees. When it comes to HR, sensitive data can include personal data such as Social Security numbers as well as privileged information concerning medical histories and more. Protecting this information is critical, making data privacy and HR security extremely necessary and important.
-
HR data can be kept more secure by:
- Making sure HR and IT work hand-in-hand
- Encrypting appropriate data
- Updating relevant HR and ER software regularly
- Maintaining periodic data security training
-
The best way is to start with an established and proven employee relations software solution. Besides being indispensable to your ER team, HR Acuity’s software solutions were designed from the ground up with data privacy and HR in mind, so you know your information is being handled properly, including:
- Configurable permissions that give you the power to control who sees what information and who does not.
- Centralized documentation that allows for more efficient and secure HR data storage. It allows all team members to be on the same page, while easily accessing the right information at a moment’s notice.
- Four levels of data protection that let you know you can be confident your information is safe and secure. We protect you at from every angle: From the servers to the software to the network to authentications, you can rest easy knowing that we take HR data security as seriously as you do.

Is HR Acuity’s Employee Relations Software Worth It? Run the Numbers.
Use our ROI Calculator to quantify the actual value of our software to your employee relations and your organization.